Comparative Study of Dash, Railgun, Aztec, Secret Network, and Aleo
The Privacy Trilemma
Every crypto privacy project is haunted by a ghost: the Privacy Trilemma. It’s the impossible balancing act between transparency, confidentiality, and auditability. Since the first generation of privacy tech—Zcash, Monero, Tornado Cash—a new wave of projects has emerged, each betting on a different way to exorcise the ghost—from architectural decisions to design philosophy. Let’s take a look at a broad taxonomy of privacy technologies.
A Taxonomy of Privacy-Enhancing Technologies
On-chain privacy solutions can be broadly categorized as follows:
Mixing and Obfuscation: An early technique, exemplified by CoinJoin, which mixes transactions from multiple users to break the deterministic link between inputs and outputs, obfuscating the transaction graph. Think of it like hiding in a crowd—its effectiveness depends entirely on its size.
Cryptographic Privacy (Software-based): This approach uses advanced cryptography for mathematical guarantees of privacy. The most prominent technology is the Zero-Knowledge Proof (ZKP), which allows a prover to prove a statement is true without revealing any information beyond its validity. Sub-categories like zk-SNARKs (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge) and their variants like PLONK (which make the setup process universal and updatable) are central to modern privacy protocols.
Confidential Computing (Hardware-based): This method relies on Trusted Execution Environments (TEEs)—essentially a digital black box inside the processor itself. Code and data go in, are processed in total secrecy, and results come out, with not even the computer's owner able to peek inside.
Architectural Privacy: This approach redesigns the blockchain’s fundamental architecture for privacy. A key example is off-chain computation with on-chain verification. Users execute sensitive computations locally and submit a cryptographic proof (typically a ZKP) to the public chain. Validators only need to verify the small proof, preserving privacy and enhancing scalability.
A Brief Overview of the Five Protocols
The five protocols examined below draw from different parts of this taxonomy. This typology offers a lens for understanding their tradeoffs.
Dash: An early pioneer implementing an optional, mixing-based privacy feature (PrivateSend) facilitated by a two-tier network of miners and Masternodes.
Railgun: An application-layer protocol on EVM blockchains using zk-SNARKs to create a smart contract-based privacy pool, balancing a “privacy as a human right” ethos with compliance tools.
Aztec Network: A privacy-first Layer 2 ZK-Rollup on Ethereum that pioneered the PLONK proving system, aiming to make privacy a programmable primitive for developers.
Secret Network: A sovereign Layer 1 blockchain using hardware-based privacy (TEEs) to enable “computational privacy,” allowing smart contracts to compute on encrypted data.
Aleo: A new Layer 1 blockchain architected for privacy from the ground up, using an off-chain computation model based on ZKPs and championing a “private by default” philosophy.
Dash
Genesis and Vision: From Darkcoin to Digital Cash
Dash was launched on January 18, 2014, by Evan Duffield as a fork of Litecoin, initially named XCoin (XCO). His motivation was to address Bitcoin’s lack of sufficient anonymity. The project soon rebranded to Darkcoin, explicitly reflecting its privacy goals. This branding, however, proved to be a double-edged sword. While attracting users interested in anonymity, it created a connotation of the illicit that hampered mainstream acceptance and attracted regulatory scrutiny. Recognizing this, the project rebranded again on March 25, 2015, to Dash—a portmanteau of “Digital Cash.” This marked a shift from anonymity to usability—a bid to become spendable digital cash, not darknet collateral. Unfortunately, the “Darkcoin” label branded Dash as shady, overshadowing its technical merit as a payments system.
Privacy Architecture: Masternode and PrivateSend (CoinJoin) Model
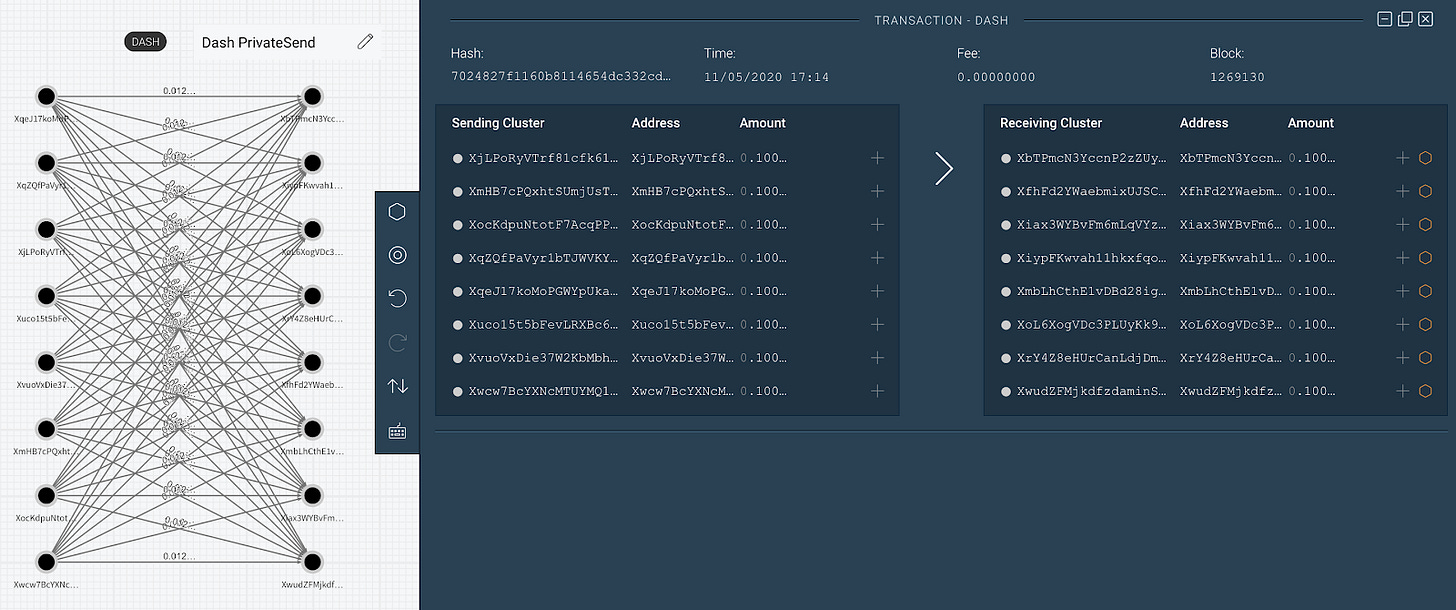
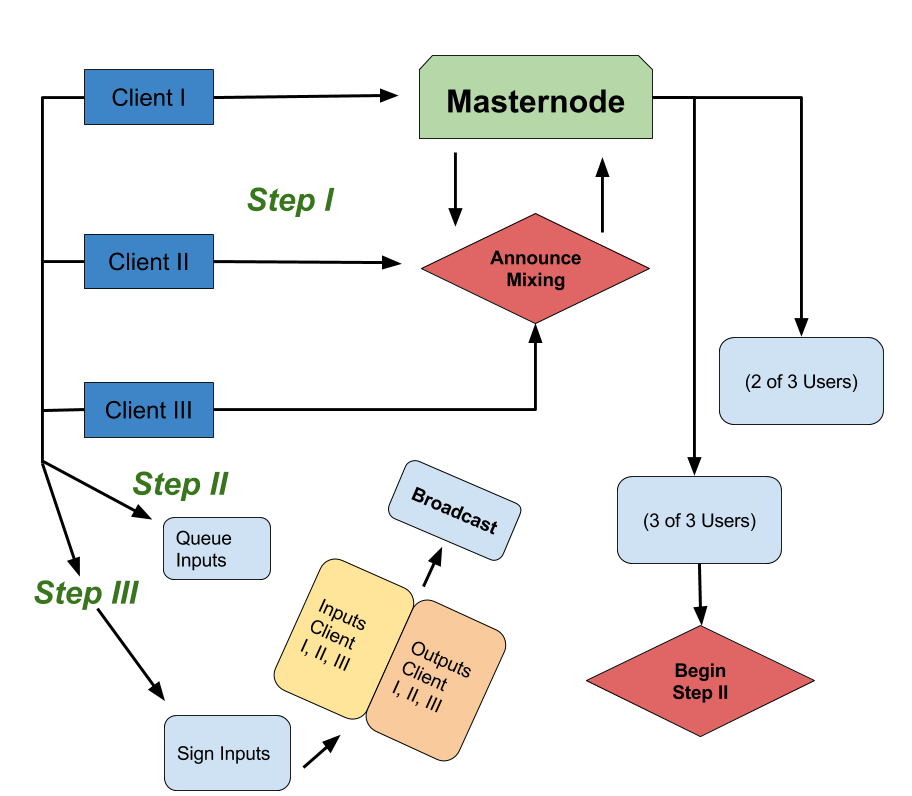
Dash’s privacy mechanism, PrivateSend, is an optional feature implementing the CoinJoin mixing technique. It aims to introduce uncertainty into the transaction graph, making it difficult to link inputs to outputs. A user’s wallet breaks down their DASH into standard denominations (e.g., 0.01, 0.1, 1, 10 DASH). During a mixing session, a Masternode gathers requests from at least two other users, coordinates a transaction where all inputs are combined, and then pays out to new addresses controlled by the same users.
Because all inputs and outputs of a given denomination are equal, it becomes probabilistically difficult to trace the flow of funds. Users can choose multiple “rounds” of mixing for greater obfuscation.
The process is non-custodial, but it relies on the Masternode network. In theory, an adversary controlling enough Masternodes could de-anonymize transactions. In practice, running a Masternode requires a 1,000 DASH collateral, making a large-scale attack expensive–the primary defence thus being economic.
Compared to modern protocols, PrivateSend’s guarantees are weak. It only obscures the direct link between inputs and outputs, not the addresses or amounts. This contrasts with Zcash’s zk-SNARKs, which can shield all transaction details. Furthermore, PrivateSend usage is optional and low (around 0.8% of transactions), limiting the anonymity set for any given mix (incidentally the exact same problem Zcash ran into).
Core Protocol Design: The Two-Tier Network, X11, and InstantSend
Dash’s most significant innovation is its two-tier network structure. The First Tier is composed of miners: this layer functions like Bitcoin’s network, with miners performing Proof-of-Work using the X11 hashing algorithm to secure the blockchain. The Second Tier is composed of Masternodes, incentivized full nodes, as operators must prove ownership of 1,000 DASH as collateral. They provide specialized services that enable key features:
InstantSend: A quorum of Masternodes locks transaction inputs within seconds, providing near-instant confirmation.
ChainLocks: A defense against 51% attacks where a quorum of Masternodes signs the first seen block at each height, preventing reorganizations.
Governance and Treasury: Masternodes form a DAO, voting on proposals and the allocation of a treasury funded by 10% of the block reward.
The block reward is split: 45% to miners, 45% to Masternodes, and 10% to the treasury DAO. This model pioneered a self-funding and self-governing protocol.
Ecosystem and Adoption Trajectory
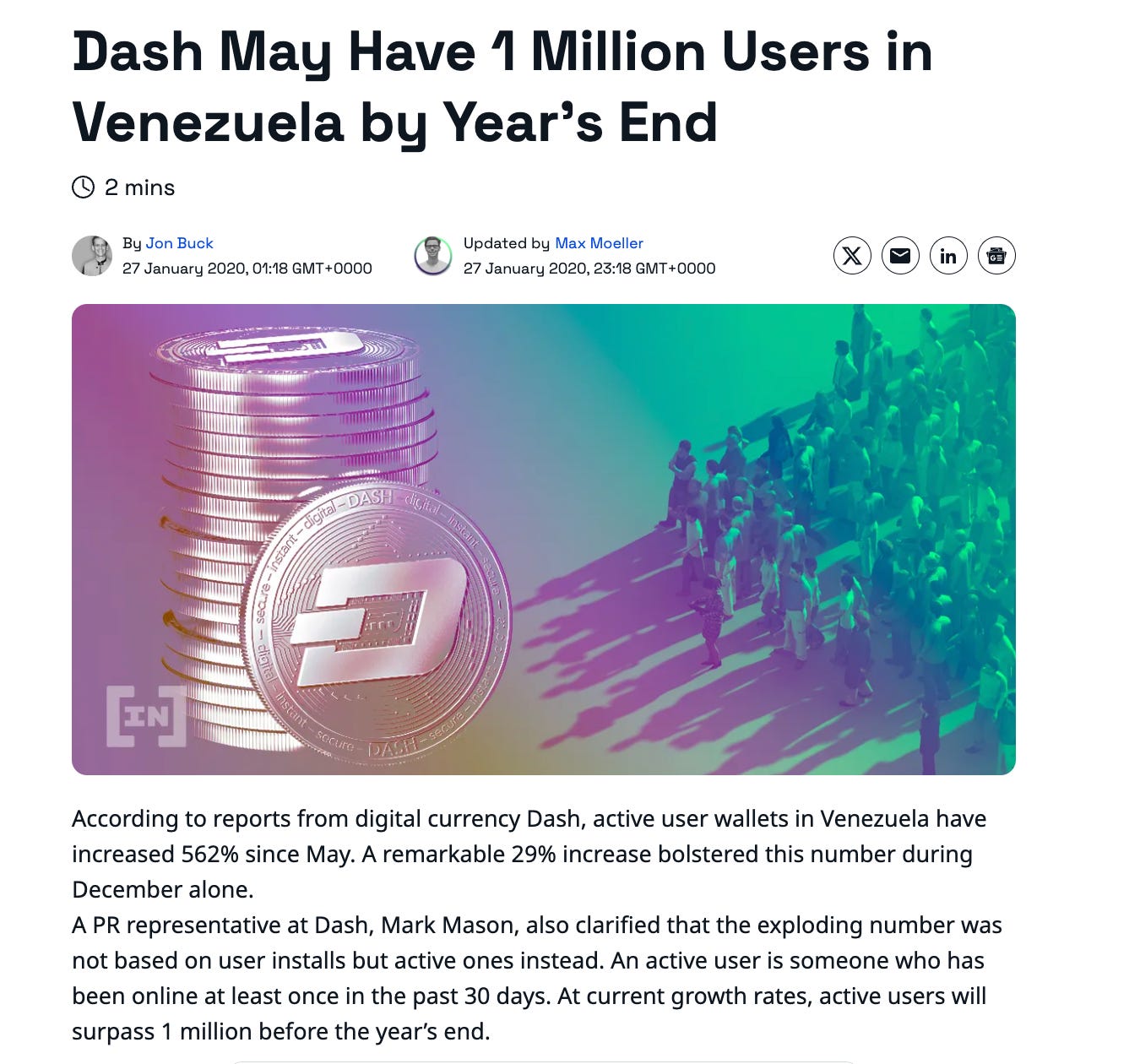
Dash has focused on being used as “digital cash” for real-world payments, especially in regions with high inflation like Venezuela.
The DashDirect app, launched in July 2021, allows users to spend DASH at over 155,000 stores by facilitating real-time gift card purchases.
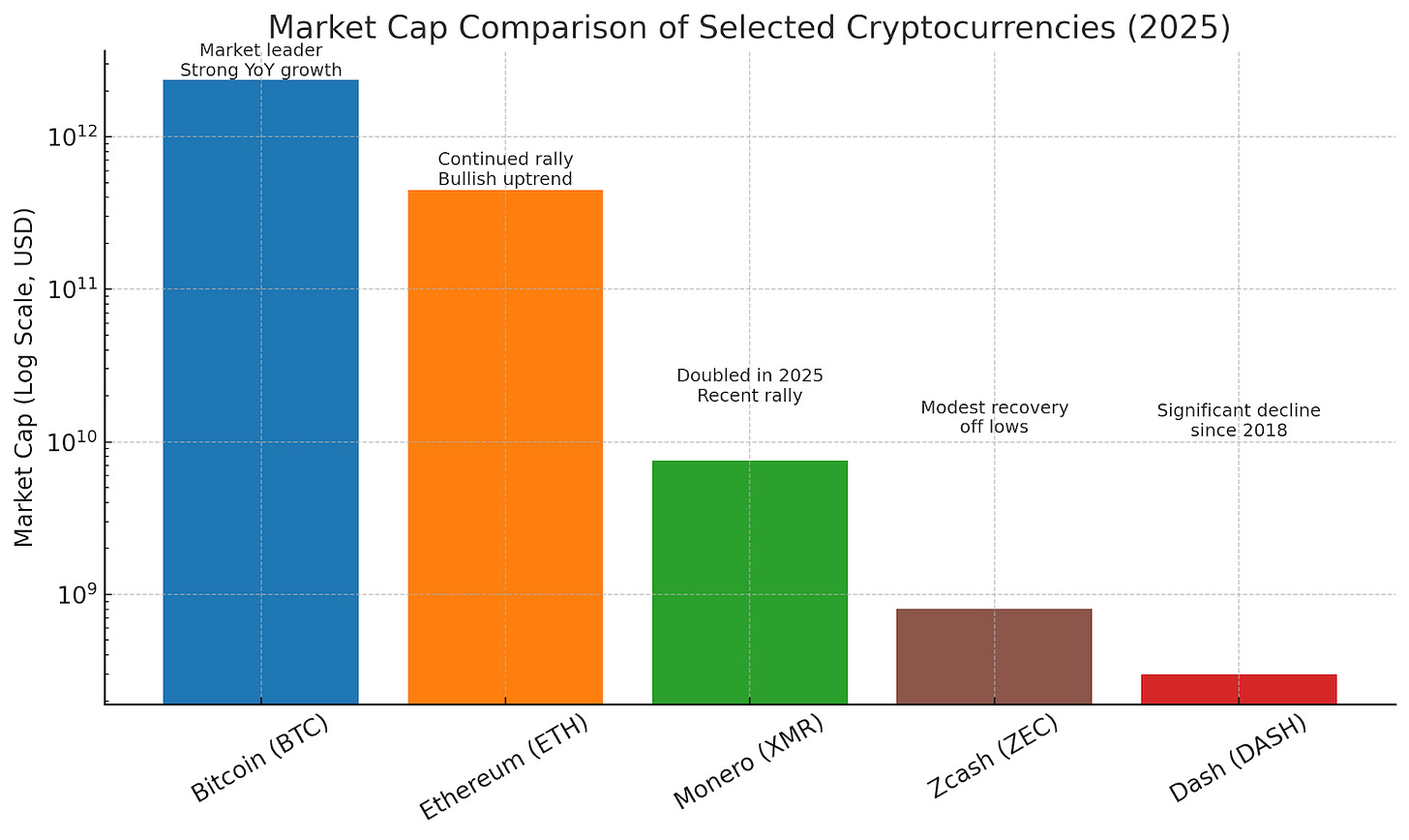
Despite these efforts, Dash has achieved niche adoption rather than mainstream traction. As of mid-2025, its market capitalization is around $300 million, placing it well outside the top 100 cryptocurrencies and reflecting a significant decline from its 2017-2018 peak. Historical data shows a project overshadowed by newer platforms.
A log scale is necessary to highlight the sheer magnitude of differences in market cap
Critical Challenges: The “Instamine” Legacy and Regulatory Misconceptions
Dash has faced two persistent challenges. First, its launch was marred by an “instamine” controversy. A bug in the difficulty adjustment algorithm allowed nearly 2 million DASH (over 10% of the total supply) to be mined within the first 24 hours. Critics have cited this as evidence of a pre-mine, creating long-term skepticism.
Second, Dash suffers from a mismatch between its technical reality and regulatory perception. In 2018, Japan’s Financial Services Agency pressured exchanges to delist Dash alongside other privacy coins. Regulators categorized it as a “privacy-centric coin,” a perception linked to its earlier “Darkcoin” history and PrivateSend feature. While its privacy is optional and weaker than true privacy coins, the project’s branding choices have caused it to be grouped with them, creating significant barriers to adoption.
Philosophical Stance: Privacy as an Optional Feature
Dash’s philosophy on privacy is pragmatic. It frames privacy not as a default state but as an optional feature to give its digital currency cash-like properties. Just as one can choose cash for a private transaction, a Dash user can choose PrivateSend, mirroring Zcash’s unshielded and shielded optionality. The goal was to improve fungibility without compromising the blockchain’s public auditability, a clear departure from privacy-by-default protocols. However, making privacy optional invites regulatory scrutiny without offering much user protection.
Railgun
While Dash represents the earliest, simplest model of obfuscation-based privacy, Railgun offers a leap forward—embedding zero-knowledge privacy directly into DeFi infrastructure, without abandoning the Ethereum ecosystem.
Genesis and Vision: On-Chain Privacy for the EVM Ecosystem
Railgun emerged in 2021 as a solution to bring privacy to Ethereum and other EVM-compatible blockchains. Founded by the pseudonymous Emmanuel Goldstein, its vision is to provide a comprehensive privacy toolkit for DeFi. It allows users to trade, lend, and interact with dApps privately without bridging assets to a separate network. This “on-platform” approach lets Railgun leverage the liquidity and security of established ecosystems like Ethereum, Polygon, and Arbitrum.
Privacy Architecture: zk-SNARKs, Private Balances, and the Broadcaster Model
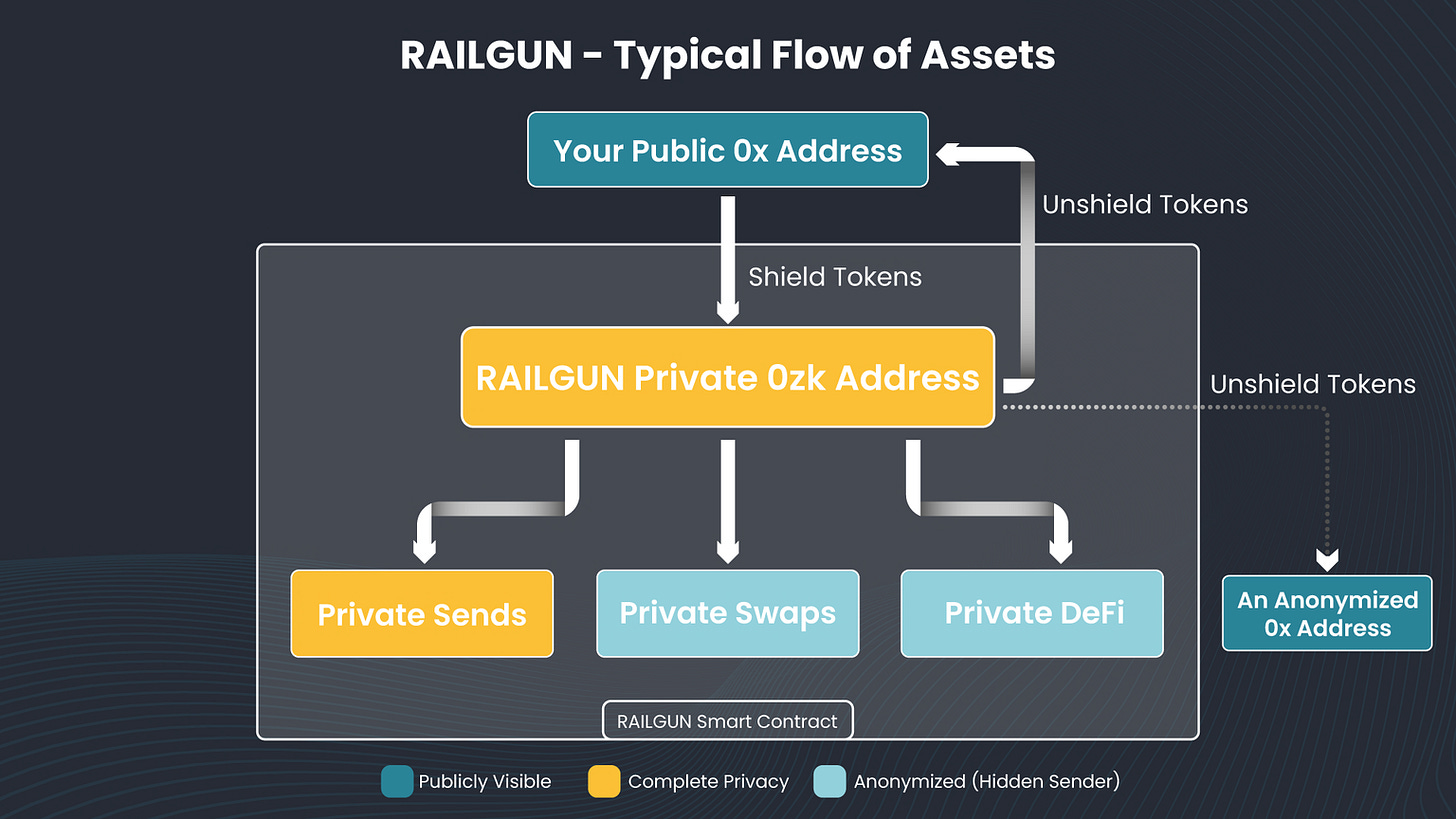
Railgun’s privacy architecture is a system of smart contracts utilizing zk-SNARKs to shield user activity. The core concept is “Private Balances.” A user “shields” tokens by transferring them into the Railgun smart contract, adding them to a large, commingled pool that serves as the anonymity set. Once shielded, the user manages their assets from a newly generated private 0zk address.
All subsequent actions from this 0zk address are private. On-chain observers only see a transaction originating from the main Railgun contract, not the user’s specific address. The attached zk-SNARK proof validates the transaction without revealing the user’s identity, balance, or history. To further enhance privacy, Railgun uses a Broadcaster Network. Users can submit transactions through independent relayers who pay the gas fee, decoupling the user’s public address (which holds gas tokens) from their private Railgun activity.
Core Protocol Design: A Smart Contract-Based Overlay
As an application layer, Railgun offers privacy as a service. It integrates directly with the most liquid DeFi ecosystems, allowing users to shield any ERC-20 token, interact privately with protocols like Uniswap, and then “unshield” back to a public address.
Ecosystem and Adoption Trajectory: The ”Vitalik Effect”, Post-Tornado Cash Era
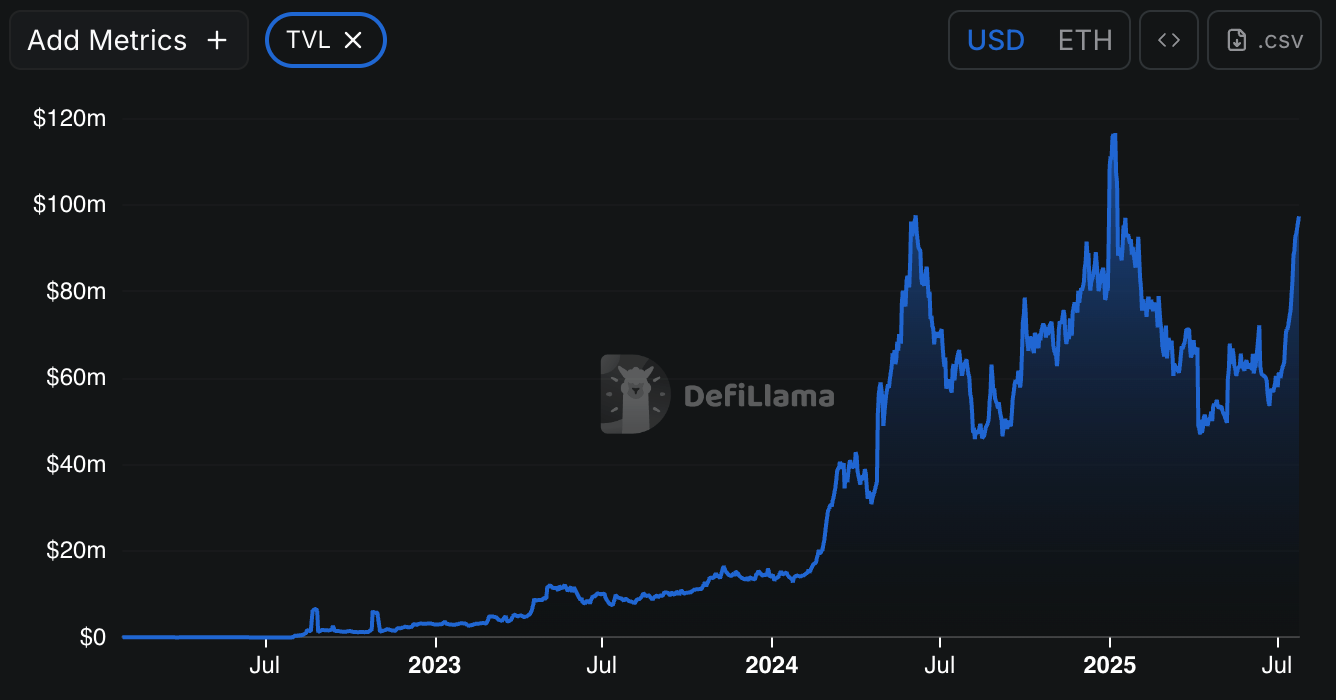
Railgun’s adoption has been explosive, driven by market events and a key endorsement. The protocol has processed over $1.16 billion in volume, with its Total Value Locked (TVL) surging over 460% in the first half of 2024 to over $76 million, reaching ~100M as of July 2025.
Two factors fueled this rise:
The Regulatory Crackdown on Mixers: In August 2022, the U.S. Treasury’s sanctioning of Tornado Cash created a vacuum in the on-chain privacy market. Railgun, with its more sophisticated features, emerged as a prime alternative.
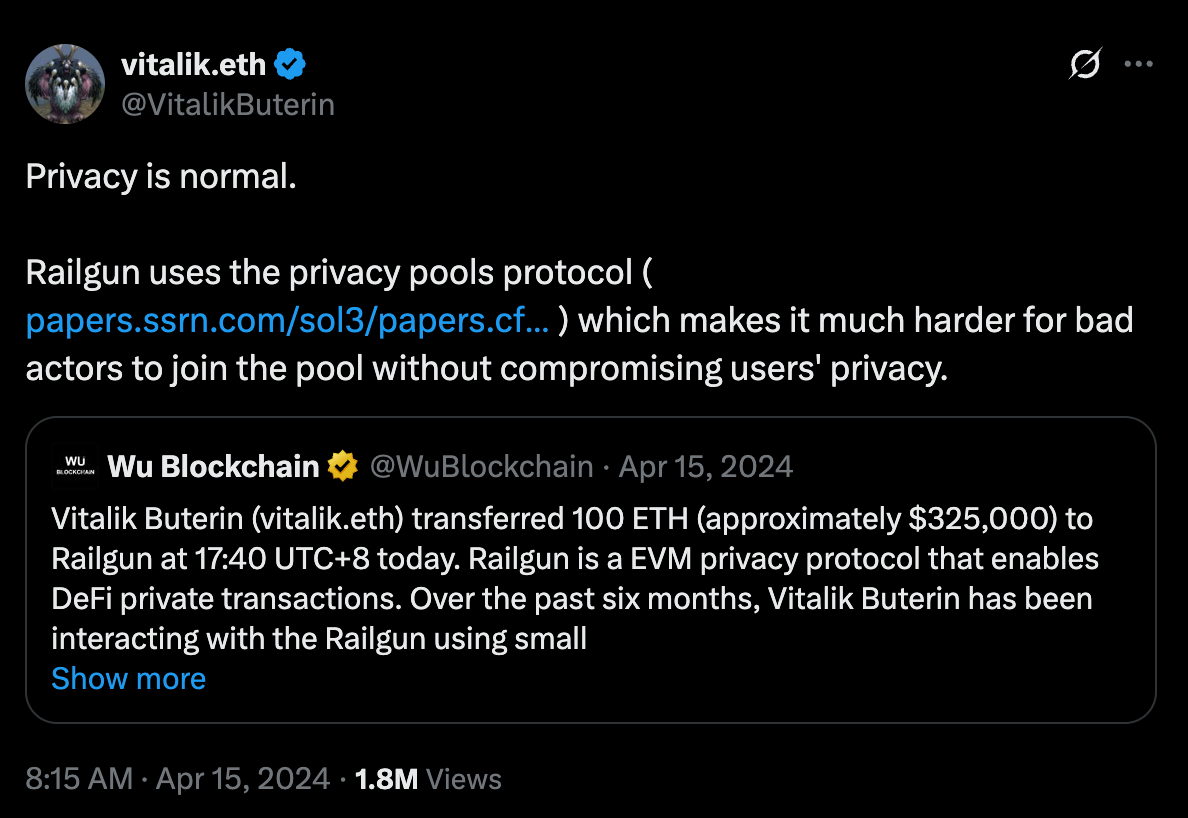
The “Vitalik Effect”: Ethereum co-founder Vitalik Buterin’s consistent and public use of Railgun provided an unparalleled credibility boost. He endorsed the protocol, stating, “Railgun uses the privacy pools protocol, which makes it much harder for bad actors to join the pool without compromising users’ privacy,” and famously declared, “Privacy is normal.” This high-profile support drove a surge in users and TVL.
Critical Challenges: “Proof of Innocence” Vulnerabilities and Reputational Headwinds
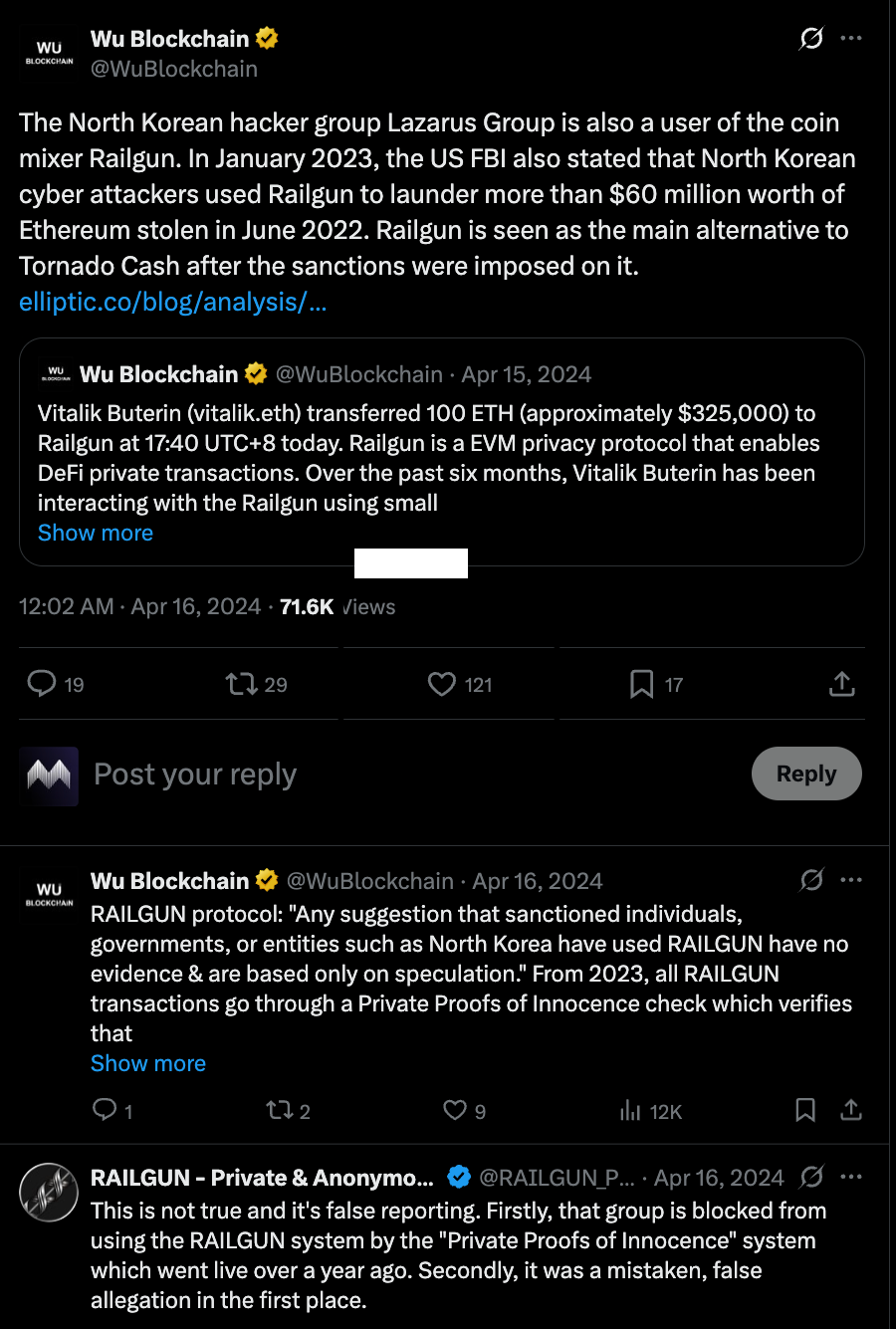
Despite its success, Railgun faces significant regulatory risk. Like Tornado Cash, it has been associated with illicit finance, with researchers alleging its use by North Korea’s Lazarus Group to launder stolen funds.
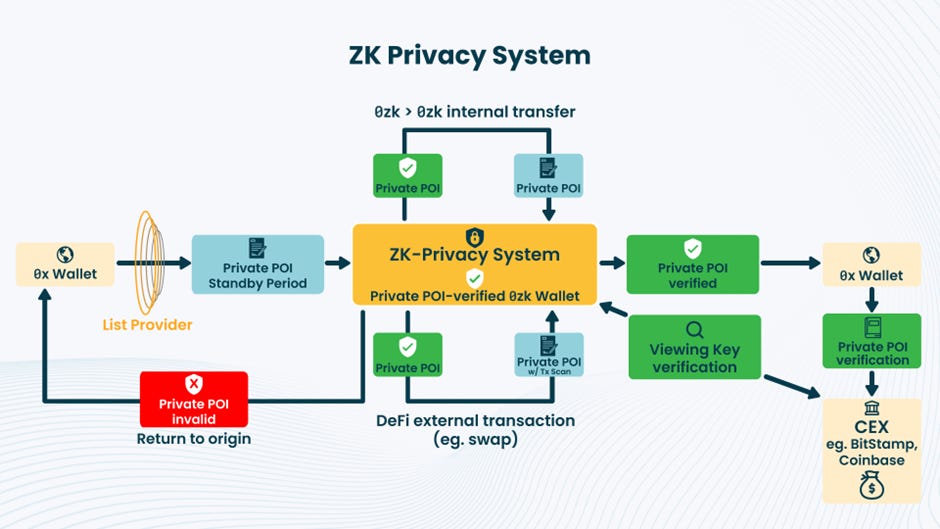
Railgun’s primary defense is its “Private Proofs of Innocence” (PPOI) system. This tool allows users to generate a ZK proof that their funds do not originate from a known list of illicit addresses, without revealing their transaction history. However, security analyses have revealed critical flaws in the PPOI design. The most significant is the “Single-Hop Dilemma”: an attacker can transfer stolen funds from a flagged address to a new, “clean” address and then shield them into Railgun. The PPOI proof will be valid, defeating the check.
This places Railgun in a state of strategic ambiguity. It promotes a “privacy as a human right” ethos while developing compliance tools like PPOI to create a defensible narrative for regulators. This balancing act could be shattered by a major illicit event that exposes the PPOI system’s flaws or by a regulatory shift deeming its vulnerabilities unacceptable.
Philosophical Stance: Privacy as a Human Right with Compliance Mechanisms
Railgun’s philosophy blends idealism and pragmatism. It frames privacy as a fundamental “human right” while acknowledging regulatory realities with tools like PPOI. The goal is to build a system with strong privacy for legitimate users while making it harder for illicit actors to abuse, creating a sustainable model for privacy under increasing regulatory scrutiny. Railgun shows how fast a good idea can grow—but without credible compliance, speed alone may just accelerate toward a wall.
Aztec Network
If Railgun retrofits privacy onto public blockchains, Aztec takes the opposite approach: it builds a privacy-native Layer 2 from first principles, with developers in mind.
Genesis and Vision: Building the Encrypted Layer for Ethereum
Aztec was founded in 2017 by Zac Williamson and Ariel Gabizon. After an initial focus on decentralized finance, the team pivoted to a more fundamental challenge: general-purpose, programmable privacy. This led to the vision for Aztec Network: a privacy-first Layer 2 scaling solution for Ethereum, designed to be the encrypted layer for Web3. Its mission is to enable developers to build fully private and scalable decentralized applications.
Privacy Architecture: The PLONK Revolution and the Hybrid State Model
Aztec’s most profound contribution is the creation of the PLONK proving system. Published in 2019, PLONK (Permutations over Lagrange-bases for Oecumenical Noninteractive arguments of Knowledge) was a breakthrough in zk-SNARK technology. Unlike earlier systems that required a unique trusted setup for every program, PLONK introduced a universal and updatable trusted setup, dramatically improving the practicality of building with ZKPs.
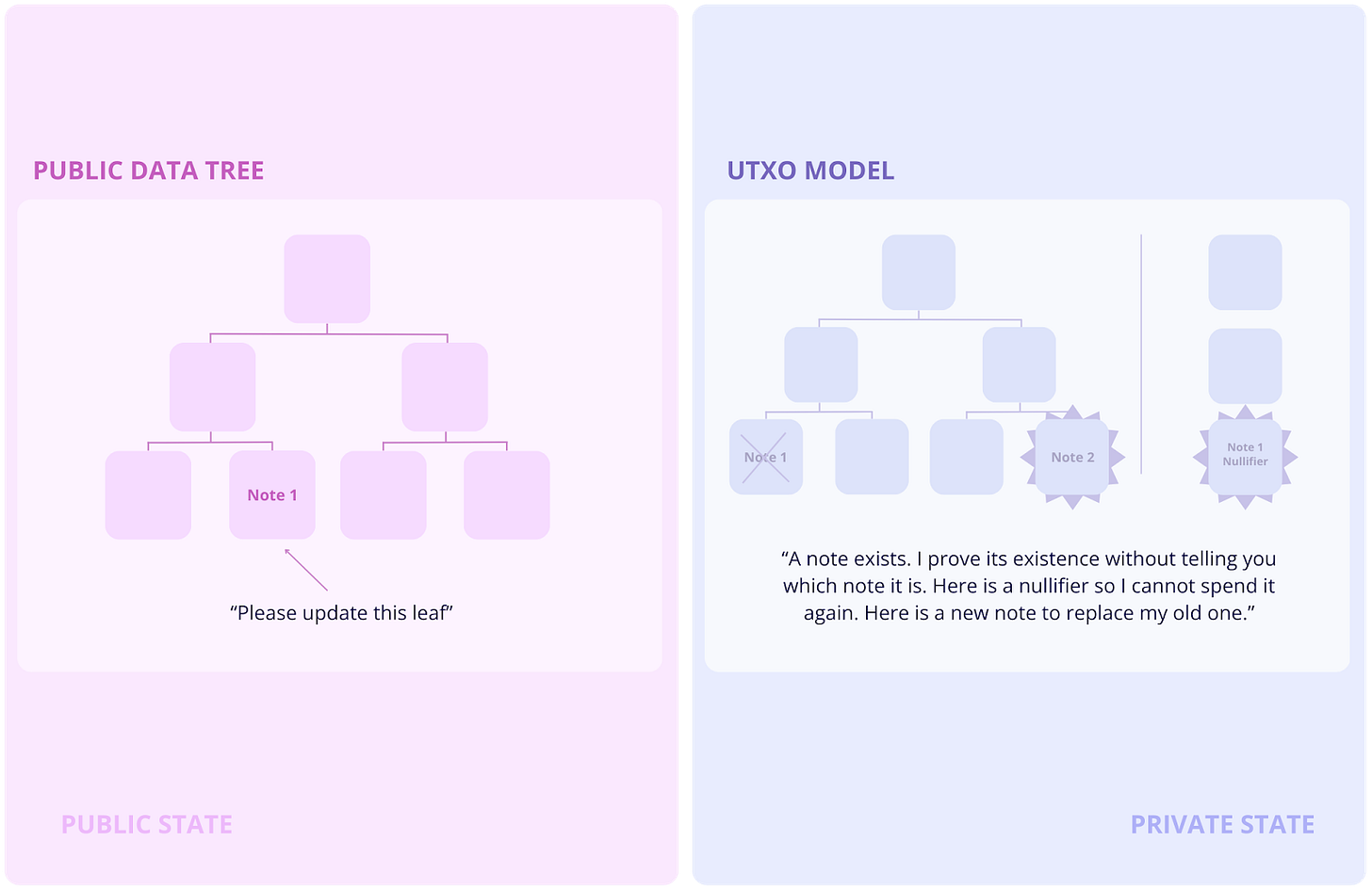
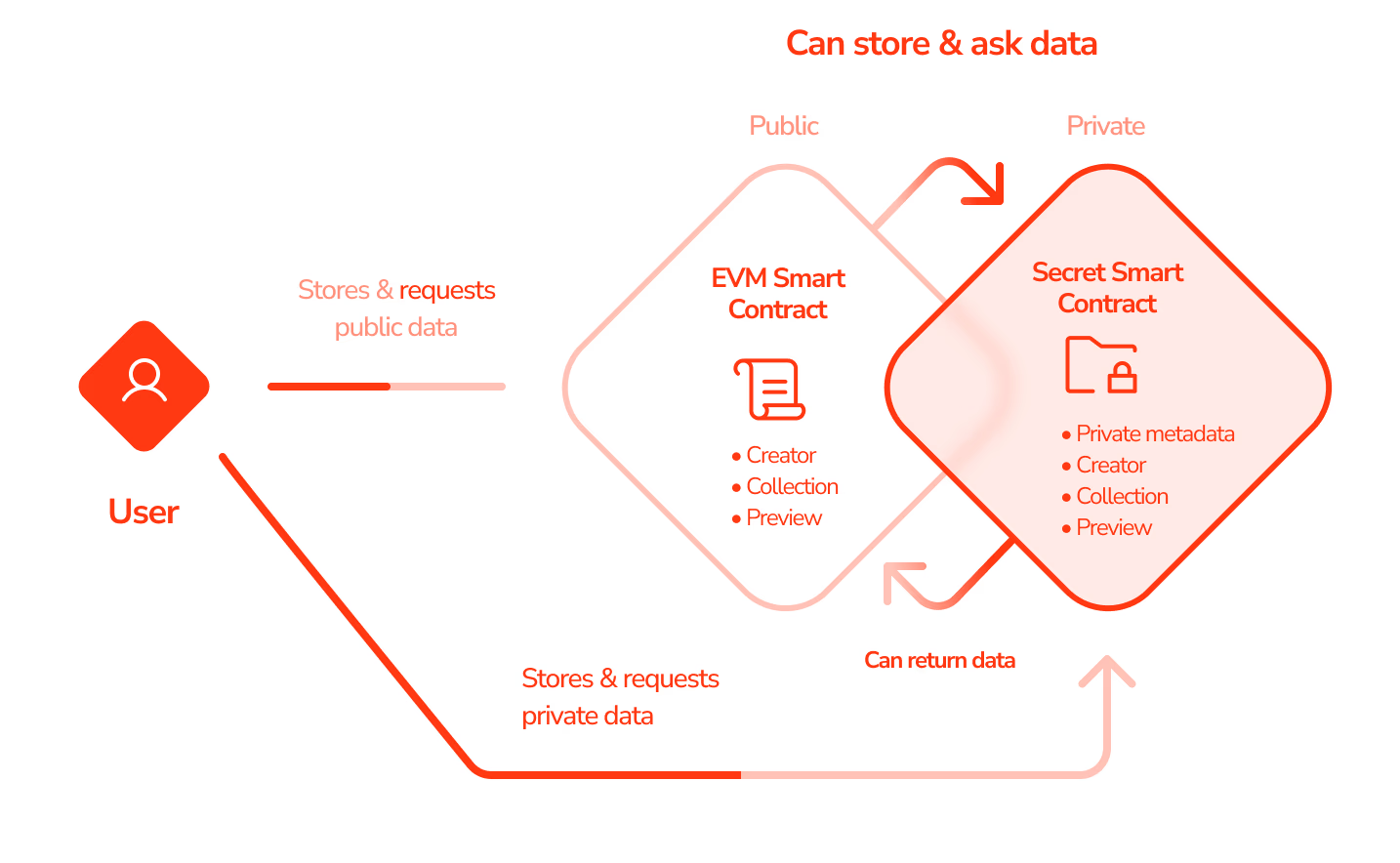
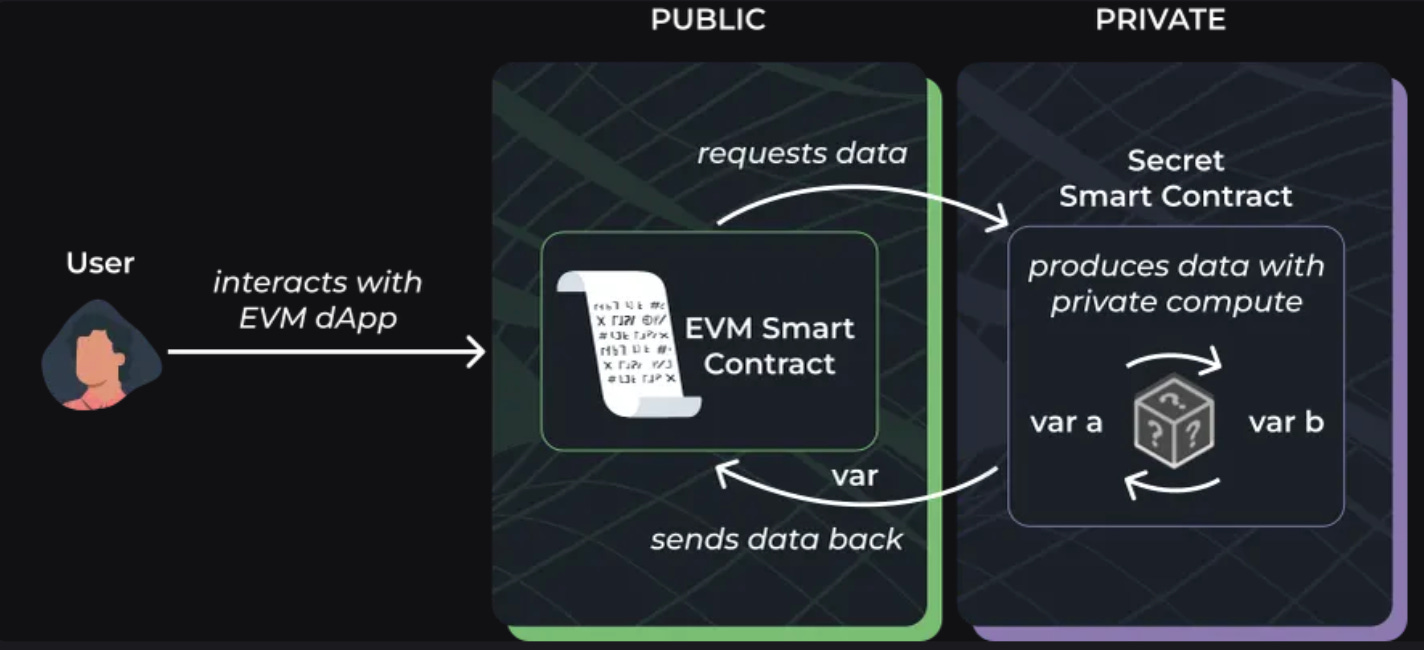
Aztec’s architecture is a ZK-Rollup. It bundles many user transactions off-chain, generates a single zk-SNARK to prove their validity, and submits this succinct proof to Ethereum. This provides significant scalability, reducing transaction costs by up to 100x while inheriting Ethereum’s security. A key feature is its hybrid state model, which supports both public and private computations by maintaining two parallel state trees: one private (using an encrypted UTXO model) and one public (like Ethereum’s account model). This gives developers the flexibility to mix confidential and public logic, a concept Aztec calls “programmable privacy.”
Core Protocol Design: The ZK-Rollup, the Noir Language, and the Sunset of Aztec Connect
To make its architecture accessible, Aztec created Noir, a domain-specific language (DSL) for writing ZK programs. Designed to be similar to Rust, Noir abstracts away the complexity of proof generation, enabling developers to build private smart contracts more easily.
Aztec gave up short-term traction in pursuit of long-term differentiation. After launching zk.money, its private transfer protocol, it rolled out Aztec Connect—a private bridge to Ethereum L1 DeFi. Then, in a bold turn, the team announced Aztec Connect would be sunset. This was a classic “burn the boats” strategy, a high-risk, high-reward bet that sacrificed a working product to force all focus onto the ultimate prize: a new, natively private platform for developers.
Ecosystem and Adoption Trajectory: Institutional Partnerships and Venture Capital Backing
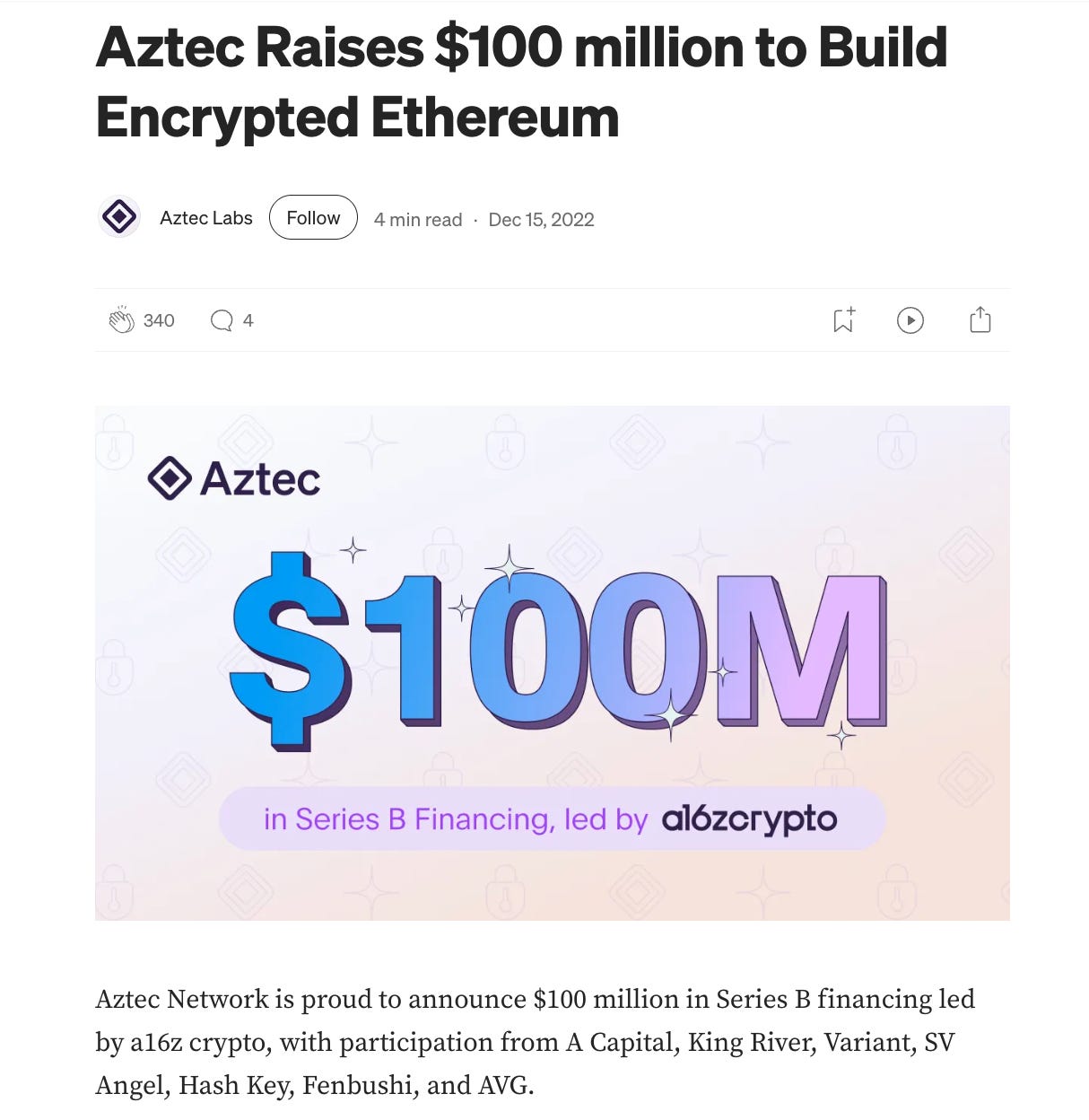
Aztec’s development is fueled by substantial venture capital backing, including a $17 million Series A led by Paradigm and a landmark $100 million Series B led by Andreessen Horowitz (a16z). This underscores deep institutional confidence in its vision.
This institutional focus is evident in its partnership with Taurus, a leader in digital asset infrastructure. In February 2025, Taurus used Aztec’s technology to release an open-source confidential token standard, allowing financial institutions to issue and manage tokenized securities privately on public blockchains. This collaboration validates Aztec’s architecture for regulated industries.
Critical Challenges: The Technical Complexity of Programmable Privacy
Aztec’s vision comes with formidable technical challenges.
Scalability and Proving Costs: Generating zero-knowledge proofs remains computationally intensive, which can create high latency and centralize the role of the prover or sequencer to entities with specialized hardware.
Developer Adoption and Tooling: The success of the new L2 depends entirely on attracting developers. While Noir simplifies ZK programming, it is still a new language with a learning curve. Building a robust developer ecosystem is paramount.
Strategic Execution Risk: Sunsetting Aztec Connect was a calculated risk. The company must now deliver on its promise of a superior, fully programmable network and successfully migrate user interest.
Philosophical Stance: Privacy as a Programmable Design Primitive
Aztec’s philosophy is that privacy should be a programmable design primitive—a fundamental building block for developers. The goal is to provide tools like Noir and the hybrid state model to allow developers to precisely control what is public and what remains private. This moves beyond simple transactional privacy to a broader concept of computational confidentiality, enabling a new design space for Web3. Aztec’s gamble is clear: if privacy is ever to go mainstream, it needs to be built for developers, not activists.
The move from Dash to Railgun to Aztec marks a shift in how privacy is conceived—not as a feature toggled by users, but as a foundational assumption of system design. Secret and Aleo take this logic to its edge, rethinking the hardware and architecture of trust itself.
Secret Network
If Aztec stakes everything on better cryptography, Secret Network makes the opposite bet: that hardware—not math—is the key to privacy at scale.
Genesis and Vision: Computational Privacy for Web3
Secret Network began as Enigma, founded in 2017 by MIT graduates. It rebranded and launched its mainnet in 2020. Its vision is to be the first blockchain with privacy-preserving smart contracts, a concept it calls “computational privacy.” Unlike protocols focused on anonymous transactions, Secret Network aims to let dApps perform complex computations on encrypted data, unlocking use cases that require confidential processing.
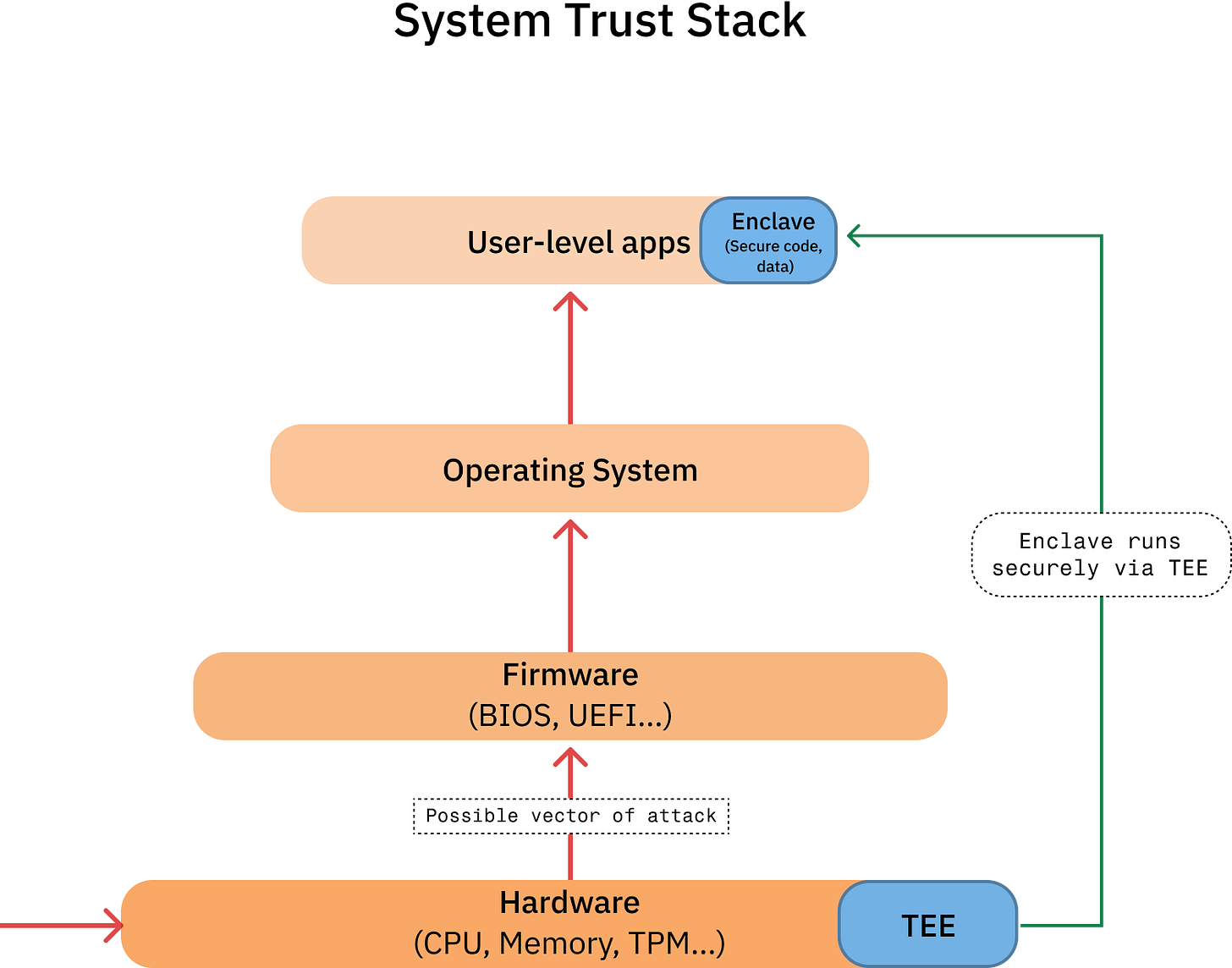
Privacy Architecture: Trusted Execution Environments (TEEs)
Secret Network’s privacy is based on specialized hardware, not software-based cryptography. It leverages Trusted Execution Environments (TEEs), specifically Intel’s Software Guard Extensions (SGX). All validator nodes must run on CPUs with Intel SGX. Smart contracts, called “Secret Contracts,” executed within these secure hardware enclaves.
User inputs are encrypted before being sent to the network. The data remains encrypted on-chain and is only decrypted inside the TEE for computation. The node operator has no access to the plaintext data. Once complete, the output is re-encrypted and written to the blockchain. Users can be given “viewing keys” to decrypt their own data or grant selective access. This TEE-based approach was a pragmatic choice, as the founders considered ZKPs and other cryptographic methods too immature and slow for general-purpose smart contracts at the time.
Core Protocol Design: The Cosmos SDK L1 and “Secret Contracts”
Secret Network is a sovereign Layer 1 blockchain built using the Cosmos SDK and Tendermint consensus. This makes it natively interoperable with the wider Cosmos ecosystem via the Inter-Blockchain Communication (IBC) protocol. “Secret Contracts,” built on CosmWasm, are the core of the network’s functionality and can be written in Rust. The native token, SCRT, is used for gas fees, staking (DPoS), and governance.
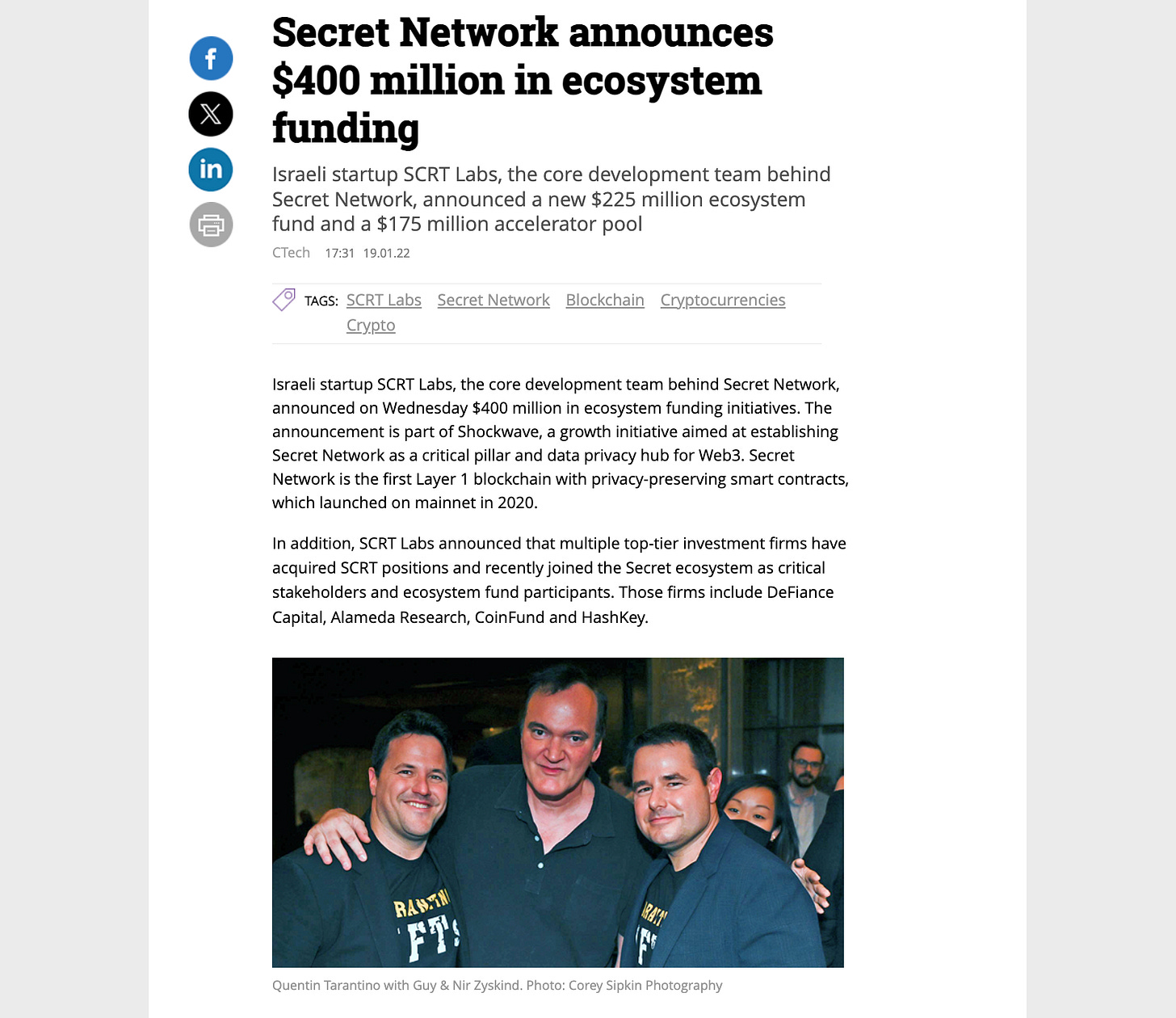
Ecosystem and Adoption Trajectory: The “Shockwave” Initiative and dApp Ecosystem
To accelerate growth, Secret Network announced the $400 million “Shockwave” initiative in January 2022, a massive ecosystem fund to provide grants and incentives. This has nurtured an ecosystem of privacy-preserving dApps, including Shade Protocol (private DeFi) and SecretSwap (a front-running resistant DEX). The network gained attention with “Secret NFTs,” which allow for private metadata, famously demonstrated in an auction of NFTs by Quentin Tarantino containing exclusive screenplay chapters from Pulp Fiction.
Critical Challenges: The SGX Vulnerability and the Trust Model of Hardware-Based Privacy
Secret Network’s primary challenge stems from its reliance on a single hardware manufacturer, Intel. The privacy model is predicated on the security of SGX enclaves. This centralized trust dependency was highlighted in 2022 when researchers disclosed the xAPIC vulnerability, a hardware bug in certain Intel CPUs. They demonstrated that this flaw could be exploited to extract the “consensus seed” from a node—a master decryption key for the entire network. Its exposure would enable an attacker to retroactively decrypt all private transactions and states, permanently compromising the network’s privacy.
The disclosure forced a public reckoning. Although SCRT Labs had worked to mitigate the threat, it was impossible to know if the vulnerability had been exploited previously. Critics argued the event exposed a fundamental flaw in the TEE-based trust model: its security is inextricably tied to a third-party technology giant, creating a unique and systemic risk profile.
Philosophical Stance: Privacy as an Enabler for Sensitive Data Computation
Secret Network’s philosophy is that privacy as a service—a tool that enables new functionality. Its focus is on creating an environment for confidential computing. The core belief is that most valuable real-world data (financial records, health data) is sensitive and will never be brought to a transparent blockchain.
By providing a platform where this data can be used in computations while remaining encrypted, Secret Network aims to dramatically expand the scope of Web3. Secret bets on TEEs not for maximalist purity, but for usable privacy in the real world—a pragmatist's choice, but one that comes at the cost of trusting Intel.
Aleo
Where Secret tries to bend today’s hardware into secure enclaves, Aleo opts for a more radical break: a blockchain designed from scratch around off-chain ZK execution and privacy-by-default.
Genesis and Vision: A “Private by Default” Internet
What if privacy wasn’t just a feature, but the foundation? Aleo takes this seriously—building a new L1 from scratch around the Zexe (Zero-knowledge EXEcution) model. Aleo was founded in 2019, with the goal of being the first real-world implementation of this model. Its vision is to build a new L1 blockchain that is private-by-default, programmable, and permissionless. The goal is to provide the foundational infrastructure for a new generation of secure, user-centric web services.
Privacy Architecture: The Zexe Model of Off-Chain Computation
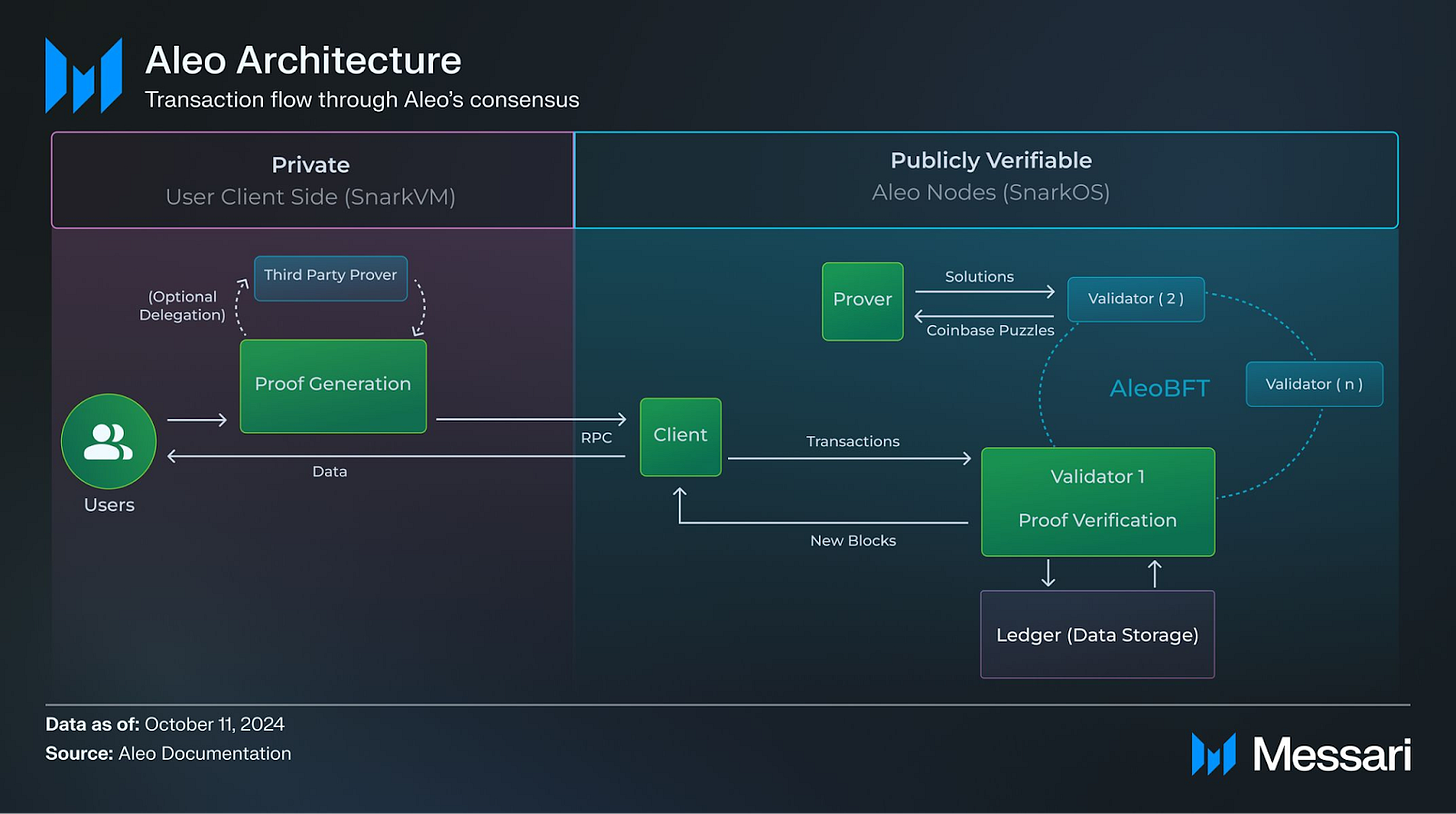
Aleo’s architectural innovation is its model of off-chain execution. Unlike Ethereum, where every node executes smart contracts, Aleo shifts the computational burden to the end-user. Users execute program logic on their own devices and generate a zk-SNARK proof attesting to the correctness of that execution. This small proof is the only thing submitted to the public blockchain.
This off-chain model buys two things at once: absolute privacy—since nothing leaves the user’s machine—and massive scalability, since the chain only verifies proofs, not computation.
Core Protocol Design: The L1, the Leo Language, and the AleoBFT Consensus
Aleo is a sovereign Layer 1 blockchain. A central component is Leo, a custom-built, statically-typed programming language inspired by Rust, designed to make writing ZK applications intuitive. The network is secured by a novel hybrid consensus mechanism called AleoBFT, which separates block production and proof generation:
Proof-of-Stake (PoS): Validators stake Aleo Credits to propose blocks and finalize transactions.
Proof-of-Succinct-Work (PoSW): “Provers” compete to solve cryptographic puzzles, which incentivizes them to generate ZK proofs, creating a decentralized market for proving.
Ecosystem and Adoption Trajectory: High-Profile Backing and a Burgeoning Developer Community
Even before its mainnet launch, Aleo garnered immense financial backing, including a $28 million Series A led by a16z and a massive $200 million Series B co-led by Kora Management and SoftBank, valuing Aleo at $1.45 billion.
This funding enabled extensive community building and incentivized testnets. A major milestone was a strategic partnership with Google Cloud, which joined the network as a validator and integrated Aleo’s data into its BigQuery service, signaling its readiness for enterprise-level applications.
Critical Challenges: The Troubled Mainnet Launch and Subsequent Community Fallout
The architectural promise was huge. The launch... was a mess. Chronic delays, accusations of insider pre-mining, and a controversial KYC requirement for its airdrop—a move seen as hypocritical for a “private by default” project—created a storm of criticism.
Compounding these issues, an inflation bug was discovered on the mainnet in November 2024, which could have allowed an attacker to create new private tokens out of thin air. While patched, its existence further damaged confidence. This series of events illustrates a profound failure in cryptoeconomic design and community management, jeopardizing the project’s decentralization and security from day one.
Philosophical Stance: Privacy as the Default State for Digital Interaction
Aleo’s philosophy is the most radical: privacy should not be an option, but the default state for all digital interaction. The project envisions a future where users have complete control over their data. By building a new L1 and the Leo language around the “private by default” principle, Aleo aims to catalyze a paradigm shift toward a fundamentally more secure and user-centric internet. Aleo promises the cleanest break from public-chain surveillance, but its launch shows that architecture alone doesn’t guarantee trust.
Comparative Analysis and Strategic Outlook
The five protocols examined represent a clear evolutionary path in the quest for on-chain privacy. They span different technological eras, architectural layers, and philosophical commitments, offering a rich landscape for comparative analysis.
The technical approaches to privacy differ dramatically, leading to varying levels of effectiveness, different trust assumptions, and unique attack vectors.
Effectiveness: The level of privacy offered exists on a spectrum. Dash’s PrivateSend provides the weakest guarantee: probabilistic obfuscation. Railgun, Aztec, and Aleo all offer strong cryptographic privacy using ZKPs, which can mathematically prove the validity of a shielded transaction without revealing its details. Secret Network’s TEE-based model also provides strong privacy, but its security is contingent on the integrity of the underlying hardware, not just the cryptography.
Anonymity Set: The strength of a privacy system is often a function of its anonymity set—the crowd within which a user hides. For Dash, this set is small and transient, consisting only of the other users participating in a specific mixing round. For Railgun and Aztec, the anonymity set consists of all assets held within their respective smart contract pools on a given chain, which can be substantial. For L1 protocols like Secret and Aleo, the anonymity set is theoretically all users of the network’s private features.
Vulnerabilities: Each model has a distinct failure mode. Dash is vulnerable to statistical chain analysis. Railgun’s compliance model (PPOI) is fundamentally flawed and can be bypassed with simple techniques. Aztec and Aleo, relying on complex ZK cryptography, are susceptible to subtle implementation bugs. Secret Network's primary vulnerability is a catastrophic failure of its trusted hardware.
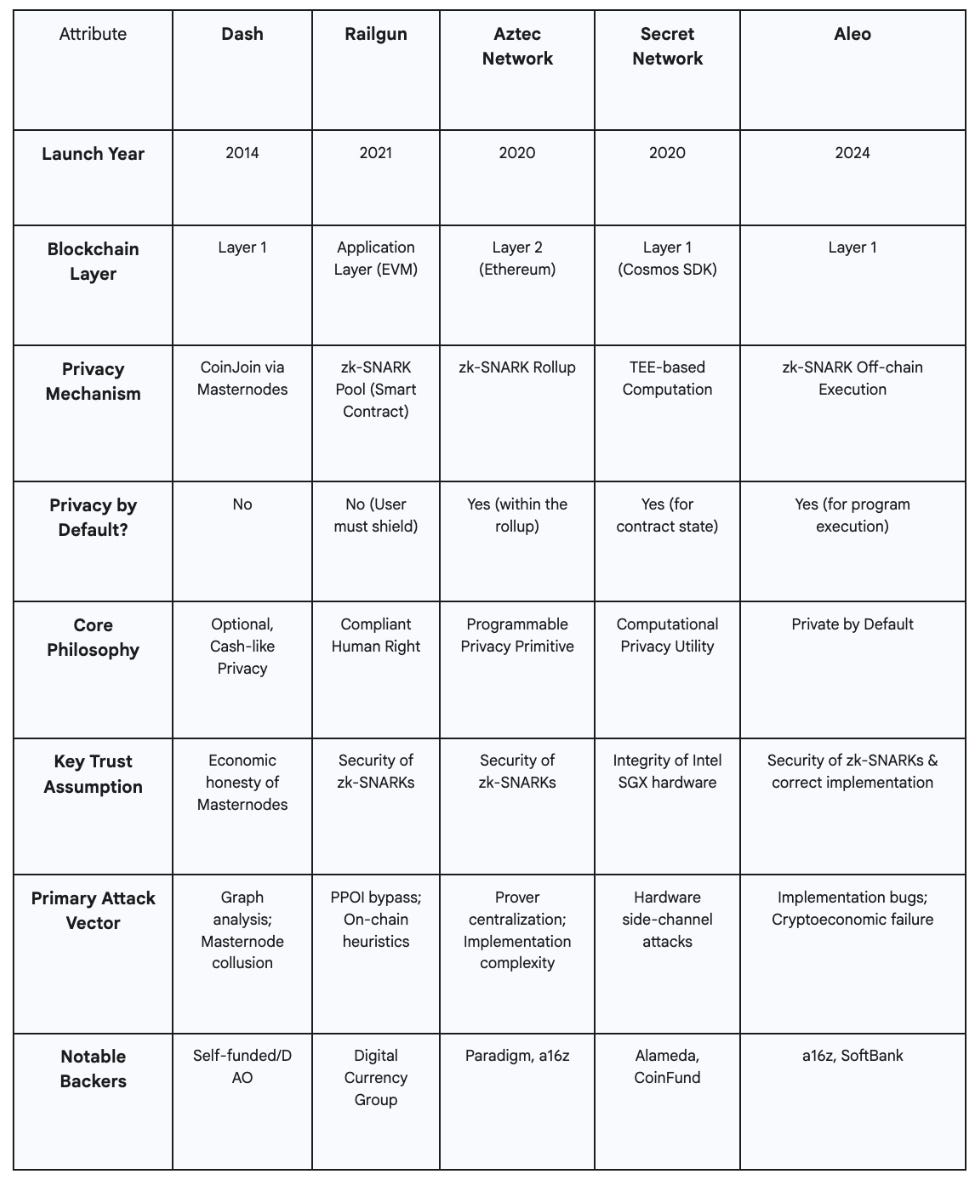
The following table provides a consolidated comparison of the core attributes, technical mechanisms, and strategic positioning of each project.
The Spectrum of Decentralization: Analyzing Architectural Trade-offs
Each protocol’s architecture impacts its decentralization. Dash’s Masternodes create a privileged class of participants. Aztec and Aleo face centralization risks around the computationally intensive roles of sequencer and prover. Secret Network’s decentralization is limited by its specific Intel SGX hardware requirements. Railgun inherits the decentralization of its host network, but its governance can be a central point of control.
Regulatory Risk Profiles: A Forward-Looking Assessment
The regulatory climate for privacy projects has long been hostile, but it is shifting. The new administration is betting on making the U.S. a global crypto powerhouse — a change that could reshape which projects thrive and which falter. Against this backdrop, Dash remains hampered by its “privacy coin” reputation. Railgun occupies a precarious gray area, its flawed compliance tools leaving it open to a crackdown. Aztec’s focus on programmable privacy for institutional partners may give it a lower risk profile, while Secret Network is similarly positioned for regulated use cases. Aleo’s mandatory KYC for its airdrop, though alienating to its community, signals a willingness to comply with U.S. rules, potentially reducing its immediate risk.
Conclusion
Future Trajectories and Key Signposts to Monitor
The future of these protocols depends on their ability to navigate their unique challenges. Key signposts to monitor are:
Dash: Can it shed its “Darkcoin” legacy to gain traction in the payments sector?
Railgun: Will regulators tolerate its “good enough” compliance, or will a high-profile illicit use case trigger a crackdown?
Aztec Network: Will its bet on programmable privacy pay off? The adoption rate of Noir and the emergence of a vibrant developer ecosystem are key metrics.
Secret Network: How will it address the systemic risk of its hardware dependency? Mitigations for future SGX vulnerabilities will be critical.
Aleo: Can the team repair the deep rift with its community? Attracting a decentralized set of provers and validators will be crucial for its long-term survival.
No project truly solves the trilemma; they just choose where to hide the trade-offs. What’s become clear is that privacy can’t be a feature bolted on at the end. It must be the starting assumption, because everything—performance, trust, and usability—flows from that single choice. Projects that forget this are doomed to reinvent the same problems, just with more complex code.
In the end, the future won't be decided by the most elegant cryptography, but by a much more human question: Which ghosts are we willing to live with?










Great analysis I’m working on a Zero knowledge proof project that uses AI for managing this system any recommendations?
https://zhtp.net/